You can get the sample from theZoo.
SHA-256: 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7
We can use behavior analysis from hybrid-analysis.

It seems there is no known protection mechanism.
In the strings, there is nothing significant other than this base64 encoded string:

The imports are not eloquent, but there is our friend GetProcAddress:

Let’s open it in IDA:
sub_403760 is used to get necessary Win API functions:

Inside sub_403760, the malware decrypts strings and uses GetProcAddress to get addresses of functions:

To decrypt strings before calling GetProcAddress, Upatre uses the following decryption routine:

Inside sub_402F30, the malware uses this technique to get addresses for the following Win API functions:
NtAllocateVirtualMemoryNtUnmapViewOfSectionCreateThreadWaitForSingleObjectLoadLibraryAHeapAllocRtlAllocateHeapRtlDecompressBufferFlushInstructionCacheNtGetContextThread
The decryption routine is used heavily by the malware in different places to obtain plain text.

At 00403572, Upatre decodes a base64 encoded string and saves it at 004051B0 (I renamed the variable to decrypted_bin):

At 0040386D, it creates a new thread:

Main work starts inside the thread at 00403900, where it decrypts and gets addresses for several Win API functions: CreateProcessW, ExitProcess, NtWriteVirtualMemory, NtSetContextThread, etc.

It creates itself as a new process in suspended mode and saves the Context:

Anti-Debugging Techniques
There is one interesting anti-debug trick. At the start, it saves the PEB and uses the BeingDebug value [PEB+2] in the XOR decryption routine. Outside of a debugger, this value is 0, and adding 0 does not cause any error. However, if we try to add 1 (which is the value of [PEB+2] if the executable is inside a debugger), it may cause an error. In this case, RtlDecompressBuffer returns 0xC0000242 (STATUS_BAD_COMPRESSION_BUFFER) error.
The reason for this error is that before calling RtlDecompressBuffer, the malware decrypts (with XOR) the decoded strings using 0x4C+[PEB+2], which is 0x4D inside a debugger instead of 0x4C, resulting in corrupted output.
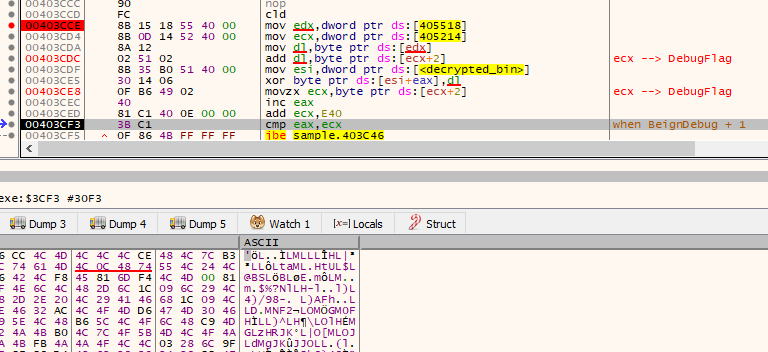
[eax+2] is the value of BeingDebug:


We can use the ScyllaHide plugin for IDA to defeat this anti-debug method.
The malware decompresses the decoded and decrypted base64 string using RtlDecompressBuffer (format COMPRESSION_FORMAT_LZNT1):

…and writes it into the suspended process:

After decompression, it calls NtSetContextThread, setting the value of EIP to 401265:

It resumes the thread and exits:

Before calling NtResumeProcess, attach x32dbg to the child process and set EIP to 401265:

Close IDA and start analyzing the child process.
The malware tries to read the uttE047.tmp file from the %TEMP% directory without success:

It creates one and writes the location of the executable:

Inside the uttE047.tmp file:
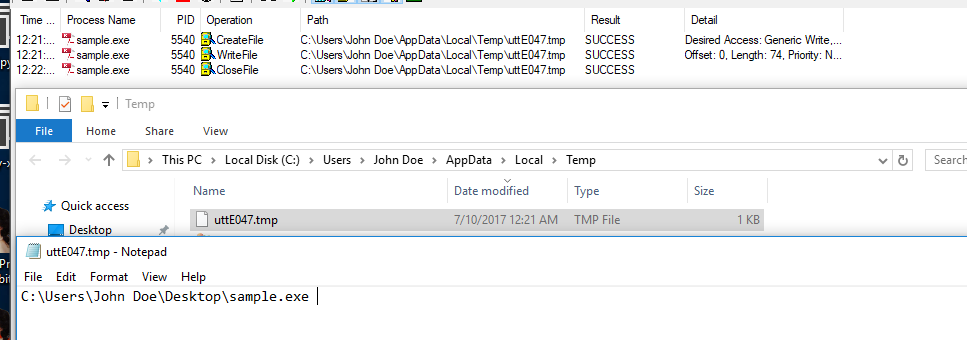
It copies the executable to the %TEMP% directory as utilview.exe:

…and creates it as a new process:

This process is exactly the same as the first process, creating a new process and injecting decoded and decompressed code.
Let’s reverse the last part (injected code) at a slightly higher level.
Now we are here: sample.exe -> sample.exe -> utilview.exe -> **utilview.exe**.
The injected code is also the same as before; it checks the uttE047.tmp file, but this time there is uttE047.tmp in the %TEMP% directory, and the malware goes in a different direction. It reads the content of uttE047.tmp, which is the location of the executable, and removes that executable:

After this, it gets the IP of the victim using checkip.dyndns.com:

Also, there is a typo in the user-agent string:

It parses the IP from the returned file:

It tries to download questd.pdf from http://penangstreetfood.net/wp-content/uploads/questd.pdf and http://yumproject.com/wp-content/uploads/2014/11/questd.pdf without success.
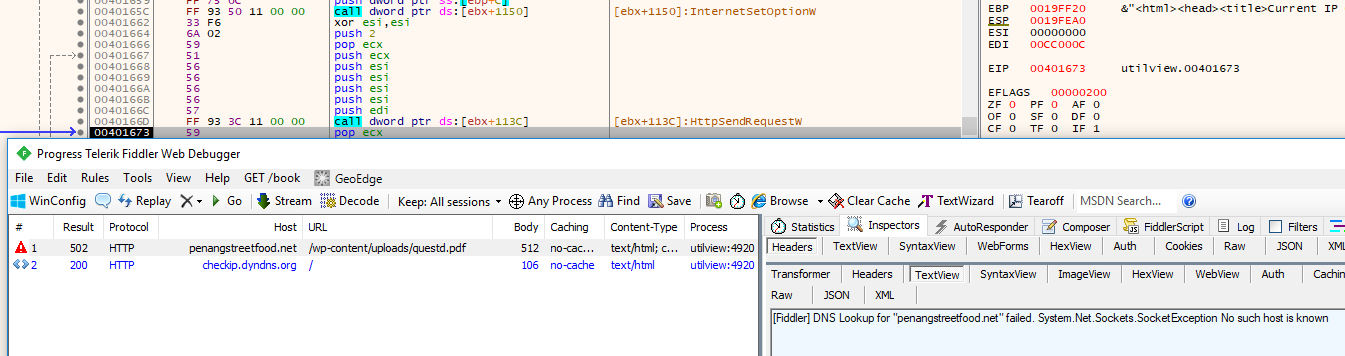
The malware sends GET requests to 95.181.46.38 with client-related information, where the last string derives from the victim’s IP address, with B instead of .:

That’s all… Upatre’s main function is to download malicious files.
Note
If you prefer, you can use my script to extract the payload instead of doing it manually:
I know I overlooked many things related to Upatre due to my limited knowledge. If you find something interesting, please contact me.
I’m new to reversing malware, and any kind of feedback is helpful for me.