Introduction
In this post, we will explore a relatively new sample of the GandCrab ransomware, which I obtained from ANY.RUN. This analysis will detail the unpacking process and the techniques employed by this malware.
Overview of GandCrab
SHA256: 643F8043C0B0F89CEDBFC3177AB7CFE99A8E2C7FE16691F3D54FB18BC14B8F45
This post serves as a light introduction to unpacking the aforementioned malware.
Memory Allocation and Code Execution
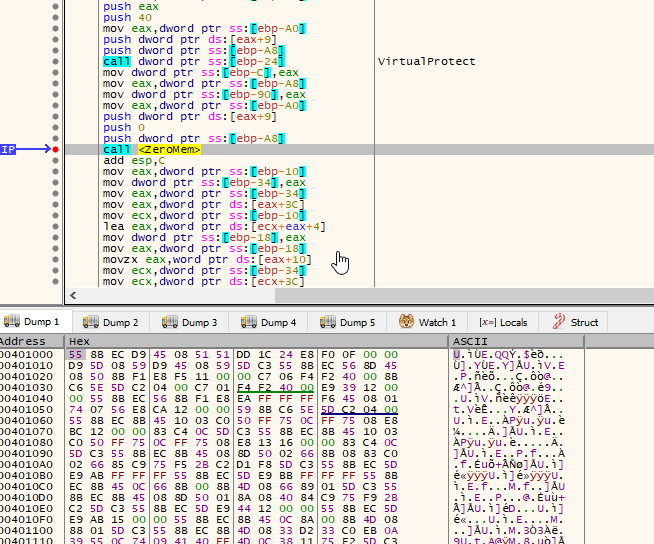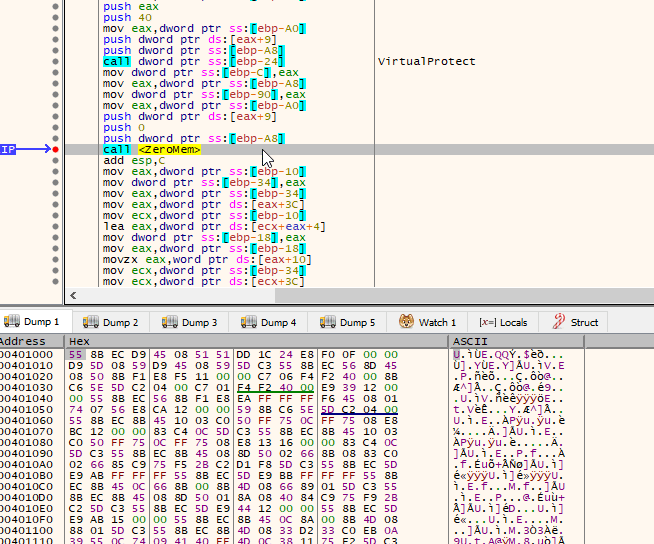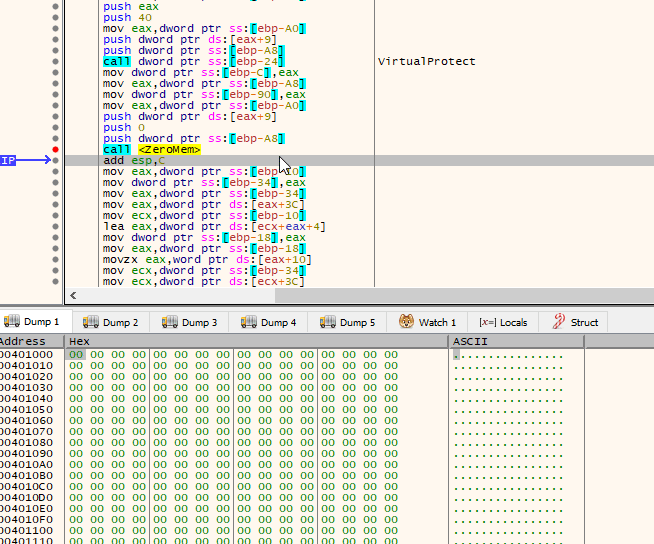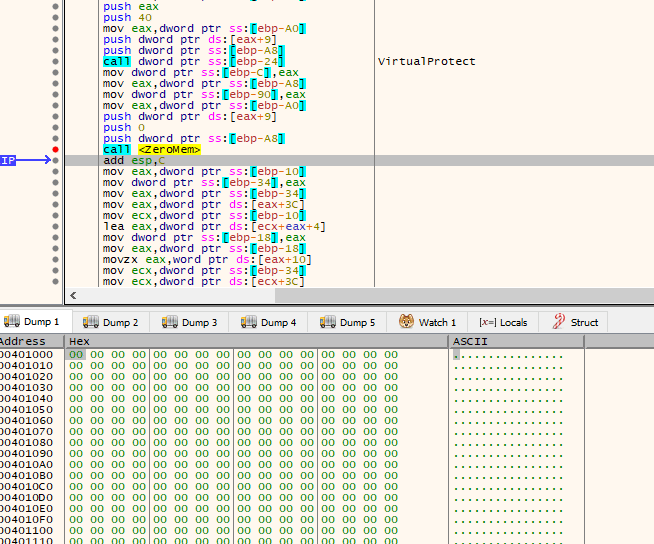
The GandCrab ransomware utilizes GlobalAlloc to allocate memory. It employs the functions at addresses 40120B and 4011E0 to decrypt and/or decode its code. After changing the memory protection to PAGE_EXECUTE_READWRITE via VirtualProtect, it jumps to the previously allocated memory using the instruction: call dword ptr ss:[ebp-68].
Functionality Breakdown
After the jump, the ransomware uses the first function to locate GetProcAddress and LoadLibrary, while the second function builds the Import Address Table (IAT) and jumps to the unpacked sample.
Locating Kernel32
Locating GetProcAddress and LoadLibrary
Locating Necessary Functions
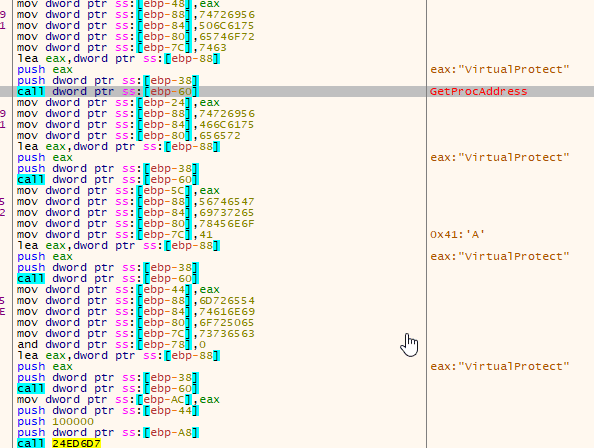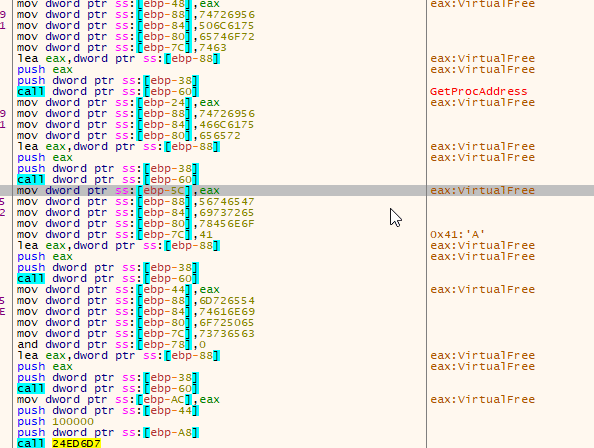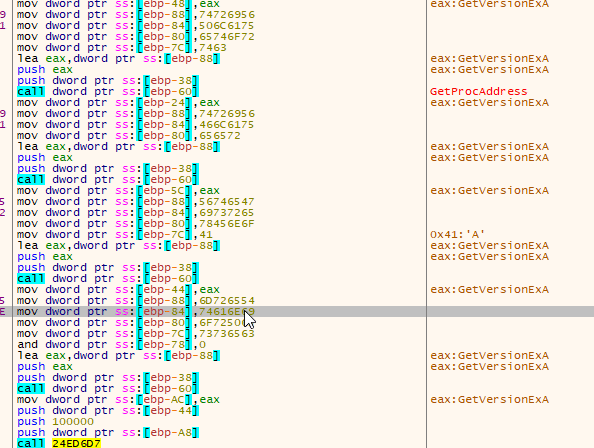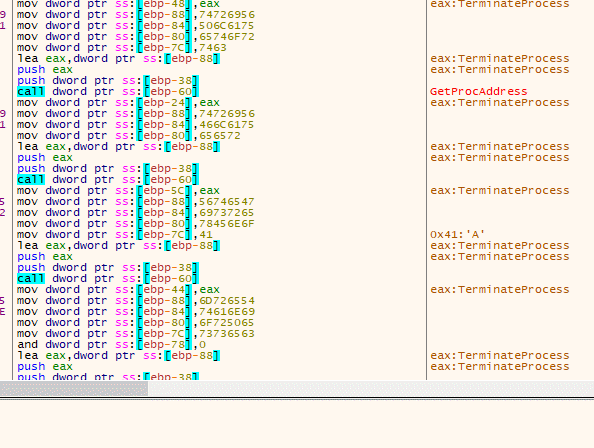
Memory Protection Changes
The ransomware changes the protection of the memory at 0x400000 (ImageBase) and removes everything from it.
Mapping New Sections
It uses a different function (at address 0x264D62E in this run) to map new sections.
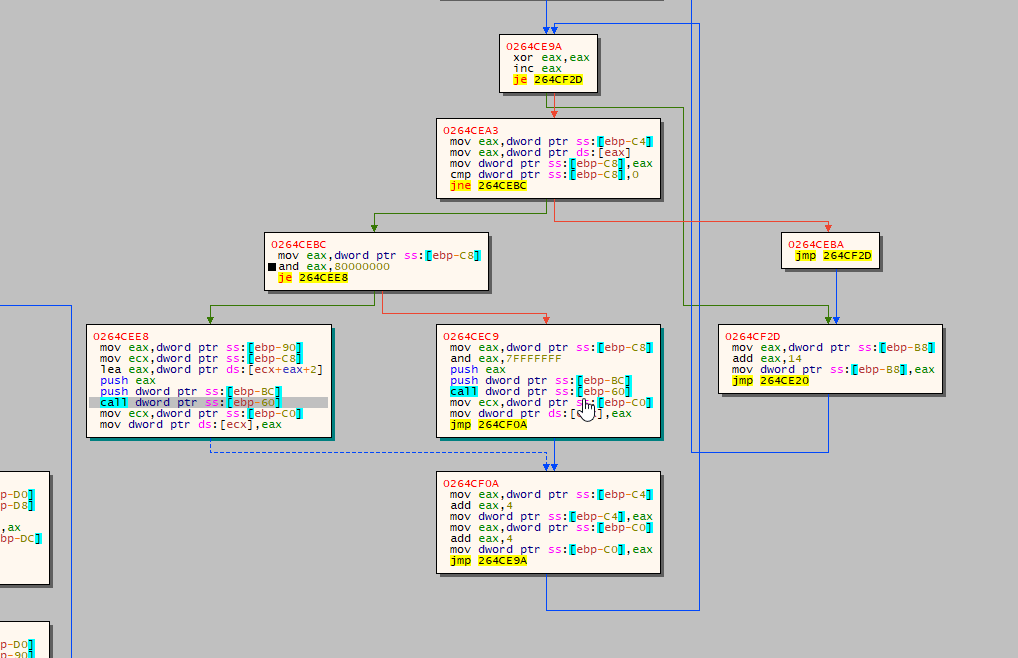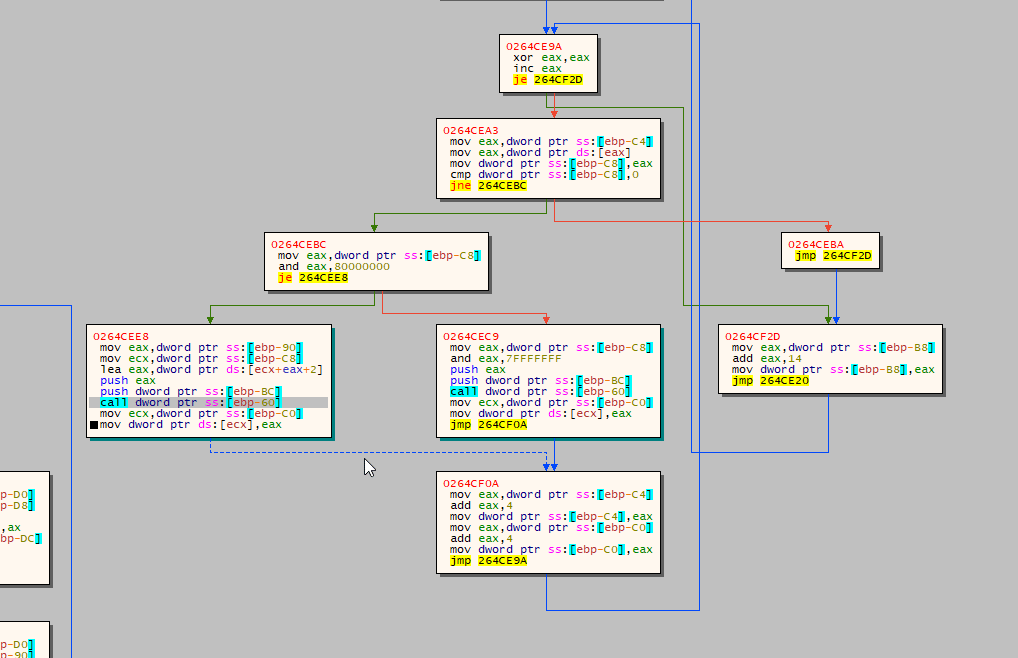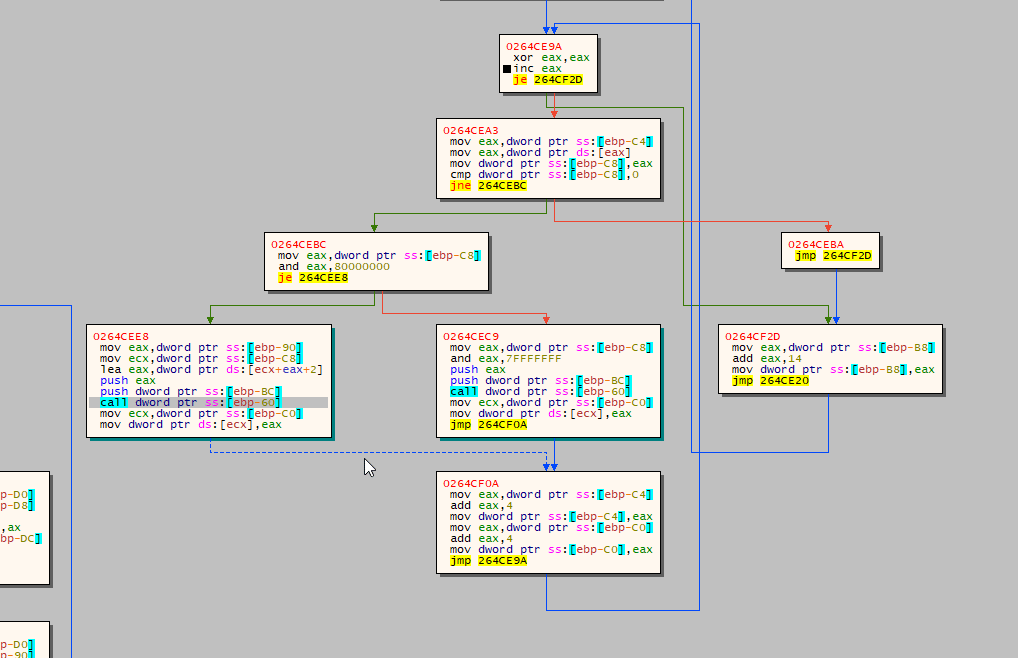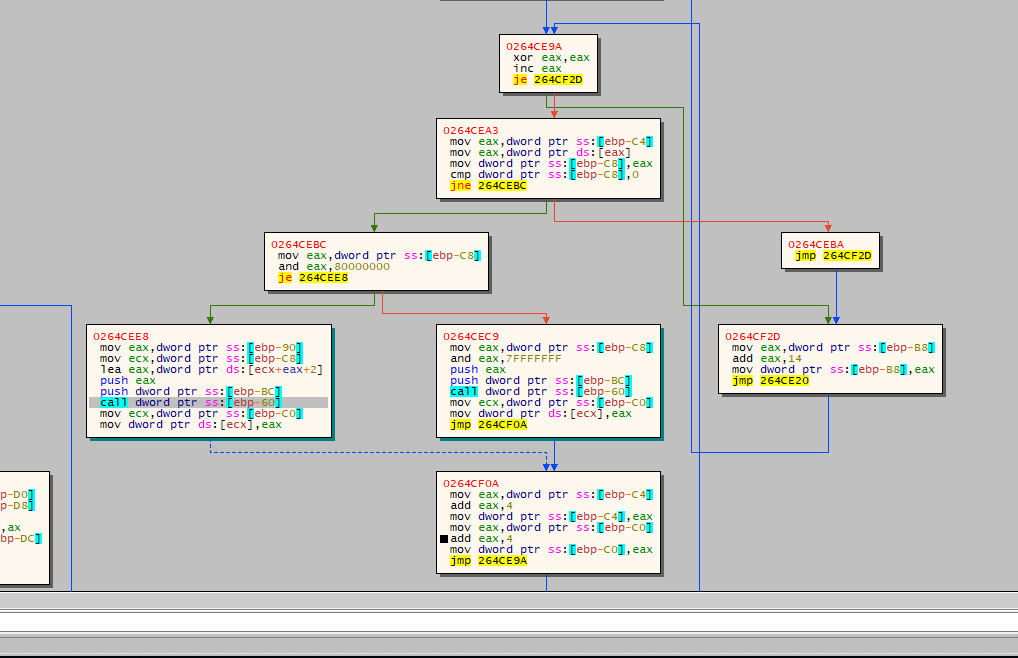
Import Address Table (IAT) Location
The ransomware locates the IAT for the recently mapped Portable Executable (PE).
Final Execution
At the end of the process, it jumps to the code located at 0x4044A5. This address was previously used by different code before unmapping the old code and mapping the new one. The debugger x32dbg handles this well.
However, in IDA, we encounter broken disassembly.
Dumping the Unpacked Version
We can use Scylla to dump the unpacked version of the ransomware.
Now, the unpacked version looks much better.